Secret sharing using the Chinese remainder theorem

Copy:
Download:
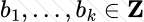
Copy:
Download:
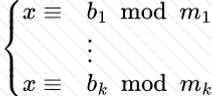
Copy:
Download:
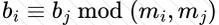
Copy:
Download:
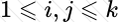
Copy:
Download:
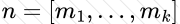
Copy:
Download:
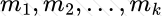
Copy:
Download:

Copy:
Download:

Copy:
Download:
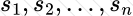
Copy:
Download:
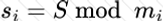
Copy:
Download:
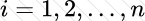
Copy:
Download:
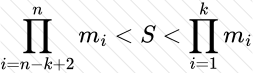
Copy:
Download:

Copy:
Download:
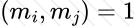
Copy:
Download:
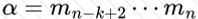
Copy:
Download:
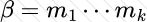
Copy:
Download:
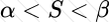
Copy:
Download:

Copy:
Download:
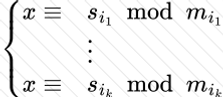
Copy:
Download:

Copy:
Download:

Copy:
Download:

Copy:
Download:
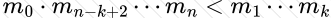
Copy:
Download:

Copy:
Download:
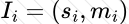
Copy:
Download:

Copy:
Download:

Copy:
Download:
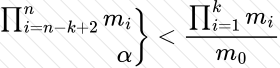
Copy:
Download:
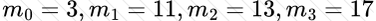
Copy:
Download:
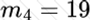
Copy:
Download:

Copy:
Download:
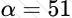
Copy:
Download:
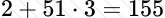
Copy:
Download:

Copy:
Download:
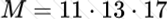
Copy:
Download:
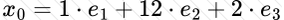
Copy:
Download:
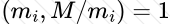
Copy:
Download:
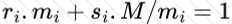
Copy:
Download:
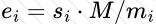
Copy:
Download:

Copy:
Download:
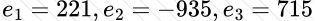
Copy:
Download:
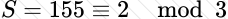
Copy:
Download: